Cybersecurity tools have become a non-negotiable part of every organization’s digital ecosystem. In 2025, as cyber threats grow more sophisticated, relying on outdated security methods is no longer an option. From nation-state attacks to AI-generated phishing campaigns, today’s threat landscape demands smarter, faster, and more adaptable tools.
Whether you’re securing a small remote team or a multi-cloud enterprise environment, the right cybersecurity technologies tools can mean the difference between a minor disruption and a catastrophic breach. These tools not only block malware or flag suspicious traffic—they actively monitor, analyze, and respond to threats in real time. In this article, we’ll walk through the 25 best cybersecurity tools to use in 2025, categorized by their core function and paired with real-world use cases.
Why Cybersecurity Tools Matter More Than Ever in 2025
The cybersecurity landscape has shifted dramatically in the last few years. With remote work now standard across industries and cloud infrastructure becoming the norm, attack surfaces have multiplied. At the same time, threat actors are leveraging automation, AI, and deepfakes to scale their attacks at unprecedented speed.
This evolution makes modern cybersecurity tools critical—not just for protection, but for proactive defense. Traditional perimeter-based strategies no longer suffice. Organizations need tools that offer real-time visibility, behavioral analytics, and automated responses. From Zero Trust architectures to identity-first security models, 2025 is the year organizations must rethink and rebuild their defense stack.
Criteria for Choosing the Right Cybersecurity Tools
Selecting cybersecurity tools in 2025 isn’t just about choosing what’s popular—it’s about finding what fits your architecture, threat profile, and compliance needs. The wrong tool can create blind spots or operational overhead; the right one can improve both security and productivity.
Here are essential criteria to consider when evaluating tools:
| Criteria | Why It Matters |
|---|---|
| Threat Detection Capabilities | Ability to identify known and unknown threats in real time |
| Integration Flexibility | Works smoothly with your existing systems and platforms |
| Compliance Support | Helps meet regulations like GDPR, HIPAA, or ISO 27001 |
| User Experience | Easy deployment, low learning curve, and clear dashboards |
| Scalability | Grows with your organization—across users, endpoints, and infrastructure |
| Response Automation | Reduces manual work and speeds up incident handling |
With these benchmarks in mind, let’s break down the top cybersecurity tools that professionals rely on in 2025.
Explore the 55 Best Cybersecurity Tools by Category and Use Case
From securing network infrastructure to detecting sophisticated threats in real-time, today’s cybersecurity landscape demands a diverse stack of tools—each specialized for different layers of protection. Below, we’ve organized 55 of the best cybersecurity tools into categories such as network security, endpoint protection, cloud defense, identity management, threat detection, and more. Each tool is presented with its main function and real-world use case to help you identify which solutions best fit your organization’s security strategy.
Network Security Tools
Network security tools form the first layer of defense in any cybersecurity strategy. These tools monitor traffic, detect anomalies, block unauthorized access, and ensure data flows securely across the organization’s infrastructure. In 2025, network-based attacks have become more targeted and stealthy, making it essential to deploy solutions that offer deep packet inspection, real-time analytics, and AI-driven detection.
Whether you’re protecting a data center, hybrid cloud, or distributed remote workforce, modern network security tools must be adaptive, scalable, and capable of managing both encrypted and unencrypted traffic. Below are some of the most widely used network security tools trusted by professionals today.
Top Network Security Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Wireshark | Packet analyzer, deep inspection, open source | Network forensics, auditing | Troubleshooting slow performance & suspicious traffic |
| Zeek (formerly Bro) | Network traffic analysis, protocol parsing | Security monitoring teams | Detecting unusual SSH and DNS behaviors |
| Tenable Nessus | Vulnerability scanning, policy compliance | Mid-size to large orgs | Identifying weak points across enterprise networks |
| Snort | Real-time traffic analysis, intrusion detection | IT teams, MSSPs | Blocking known malicious IPs and attack signatures |
| Suricata | IDS/IPS/NSM with multi-threading support | High-traffic environments | Detecting lateral movement in segmented networks |
These tools don’t just monitor—they actively defend. With visibility into every packet, security teams can respond faster and prevent damage before attackers gain a foothold.
Endpoint Security Tools

Endpoints are the most common entry point for cyberattacks. From remote laptops and smartphones to Internet of Things (IoT) devices and point-of-sale systems, each endpoint is a potential vulnerability. As organizations expand their remote and hybrid workforces in 2025, endpoint security tools play a vital role in defending users and devices from malware, ransomware, and zero-day threats.
Modern endpoint security goes far beyond antivirus. It now includes behavior monitoring, real-time threat intelligence, rollback features, and even offline protection. These tools are built to detect suspicious activity before it escalates—protecting not just devices, but the sensitive data they carry.
Top Endpoint Security Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| CrowdStrike Falcon | Cloud-native EDR, threat graph, AI-driven detection | Enterprises, remote workforces | Detecting fileless malware across distributed endpoints |
| Bitdefender GravityZone | Machine learning, sandboxing, centralized control | SMBs and MSPs | Blocking ransomware before it executes on laptops |
| SentinelOne Singularity | Autonomous EDR/XDR, rollback, active remediation | DevSecOps teams | Reversing changes after a malicious process is detected |
| Sophos Intercept X | Exploit prevention, deep learning, managed detection & response | Hybrid infrastructure | Stopping credential theft via malicious browser exploits |
| Microsoft Defender for Endpoint | Native Windows protection, threat analytics, EDR | Enterprises using Microsoft 365 | Integrating seamlessly with Microsoft security ecosystem |
In 2025, endpoint protection is about prevention, detection, and rapid recovery. These tools ensure that even if a threat bypasses one layer, it won’t go undetected—or uncontained.
Cloud Security Tools

As organizations migrate more workloads to public and hybrid clouds, cloud security tools have become essential for safeguarding data, workloads, and identities across dynamic environments. In 2025, cloud threats include misconfigurations, unauthorized access, lateral movement, and even supply chain compromises—all of which require specialized tools to detect and mitigate.
Cloud security tools offer visibility into cloud configurations, enforce policy compliance, secure APIs, and detect suspicious activities in real time. With multi-cloud strategies becoming the norm, these tools are critical for maintaining a consistent security posture across AWS, Azure, GCP, and private cloud platforms.
Top Cloud Security Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Palo Alto Prisma Cloud | CSPM, CWPP, container & serverless security | Enterprises using multi-cloud | Preventing misconfigured S3 buckets from exposing sensitive data |
| Lacework | Behavioral anomaly detection, workload security | DevOps teams, cloud-native apps | Detecting unauthorized changes to cloud storage configurations |
| Wiz | Agentless scanning, risk prioritization, identity exposure | Security teams, compliance auditors | Finding exposed secrets across Kubernetes and CI/CD pipelines |
| Check Point CloudGuard | Posture management, threat prevention, IAM security | Regulated industries | Enforcing least-privilege access across hybrid cloud environments |
| Orca Security | Side-scanning, vulnerability detection, no agents needed | Fast-scaling cloud environments | Identifying and remediating high-risk assets across Azure & GCP |
Cloud security isn’t just about protecting infrastructure—it’s about maintaining visibility, enforcing policy, and securing dynamic assets that change by the minute.
Application Security Tools

In 2025, applications are a prime target for cybercriminals. Whether it’s a web platform, mobile app, or API endpoint, attackers are constantly probing for logic flaws, injection points, and vulnerabilities. Application security tools help developers and security teams catch weaknesses before attackers do—ensuring the software you deploy is both functional and fortified.
These tools range from static analysis scanners and dynamic testing tools to web application firewalls and runtime protection. Their goal: identify misconfigurations, enforce secure coding practices, and block exploitation attempts in real time without disrupting performance.
Top Application Security Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Burp Suite Professional | Web vulnerability scanning, manual testing support | Security researchers | Identifying SQL injection and XSS vulnerabilities in web portals |
| OWASP ZAP | Open-source DAST, automation, active/passive scanning | DevSecOps, QA teams | Integrating into CI/CD pipelines for automated scanning |
| Veracode | SAST, DAST, software composition analysis | Enterprises with large codebases | Enforcing secure coding practices during software development |
| Akamai App & API Protector | WAF, bot protection, API security | High-traffic web applications | Blocking malicious bots targeting login endpoints |
| Synopsys Coverity | Static code analysis, compliance support | Regulated industries | Ensuring code-level security for embedded software in medical devices |
With the rise of DevSecOps and API-first development, application security tools are no longer optional—they’re a necessary part of delivering secure, resilient software.
Identity & Access Management (IAM) Tools

Identity is the new security perimeter. As more users access sensitive data from various devices and locations, controlling who has access to what—and when—has become a cornerstone of cybersecurity. IAM tools help organizations enforce least-privilege access, prevent credential misuse, and ensure compliance with access governance policies.
In 2025, IAM tools are increasingly integrated with AI, behavioral analytics, and zero-trust frameworks. They manage user authentication, authorize resource access, and detect anomalies that signal potential breaches. Whether you’re managing thousands of remote workers or integrating third-party services, IAM solutions are essential for secure operations.
Top IAM Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Okta Identity Cloud | SSO, MFA, lifecycle management, adaptive access | Large and hybrid enterprises | Enabling secure, frictionless login for global remote teams |
| Microsoft Entra ID | Identity governance, conditional access, MFA | Microsoft 365 environments | Enforcing conditional access policies based on device and location |
| Auth0 (by Okta) | Developer-friendly IAM, API security, extensible rules | SaaS providers, app developers | Securing user authentication for a large-scale customer platform |
| Ping Identity | Identity federation, passwordless login, zero trust | Regulated industries | Centralizing IAM across multiple on-prem and cloud applications |
| CyberArk | Privileged access management, session recording | High-security environments | Managing and auditing administrator-level access to critical systems |
IAM tools don’t just grant access—they monitor, enforce, and adapt based on user behavior and risk context. In the modern cybersecurity landscape, strong identity controls are non-negotiable.
SIEM & XDR Tools
As cyber threats grow more sophisticated, security teams need more than firewalls and endpoint protection—they need visibility across the entire attack surface. That’s where SIEM (Security Information and Event Management) and XDR (Extended Detection and Response) tools come in. These solutions collect, correlate, and analyze data from across the infrastructure to detect suspicious activity and enable rapid response.
In 2025, SIEM and XDR tools are merging machine learning, threat intelligence, and automation to help analysts cut through alert fatigue and respond to threats in real time. They serve as a central nervous system for modern SOCs (Security Operations Centers), enabling end-to-end detection and coordinated incident response.
Top SIEM & XDR Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Splunk Enterprise Security | Real-time data ingestion, threat correlation, adaptive analytics | Large SOC teams, MSSPs | Detecting APT activity across hybrid infrastructure |
| Microsoft Sentinel | Cloud-native SIEM, ML analytics, built-in threat intelligence | Microsoft ecosystem | Investigating lateral movement in Azure environments |
| IBM QRadar | Log management, advanced correlation, AI-assisted investigation | Highly regulated industries | Identifying internal threat actors using behavior patterns |
| Elastic Security | Open-source SIEM/XDR, MITRE ATT&CK integration | Elastic Stack users | Investigating threats across logs, metrics, and endpoint telemetry |
| Trend Micro Vision One | Unified XDR, risk insights, threat detection across vectors | Enterprises with large attack surfaces | Correlating endpoint, email, and network alerts for faster response |
Modern SIEM and XDR tools help reduce detection and response times, centralize threat visibility, and enable proactive defense—making them critical in the evolving cyber threat landscape.
Vulnerability Management Tools
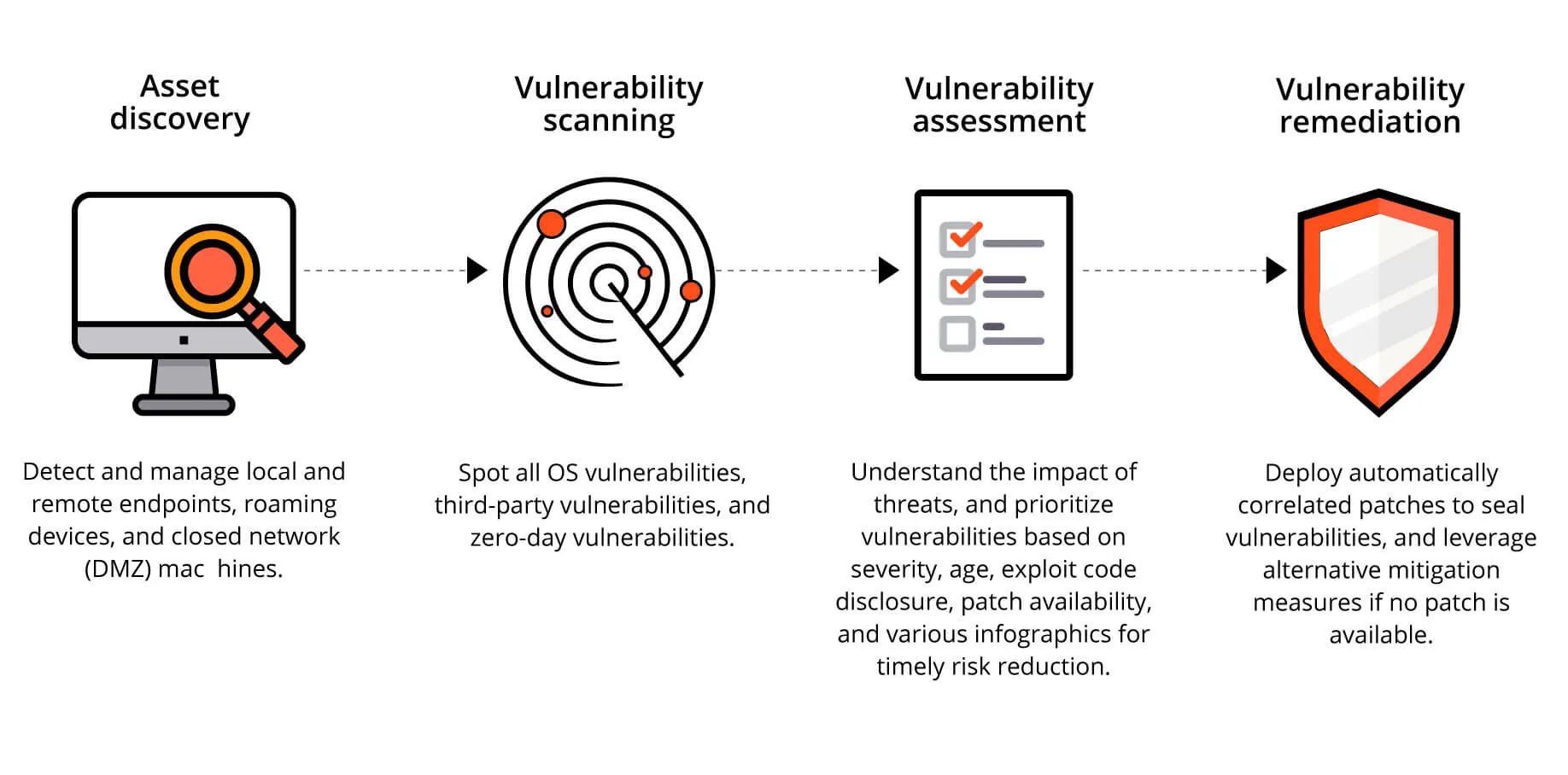
In cybersecurity, unpatched vulnerabilities are among the most exploited attack vectors. Whether it’s outdated software, misconfigured systems, or forgotten endpoints, attackers are always looking for a way in. Vulnerability management tools help identify, prioritize, and remediate these weaknesses before they’re leveraged in an attack.
By continuously scanning networks, applications, and assets, these tools provide visibility into known and emerging threats. In 2025, the most effective solutions combine threat intelligence, risk scoring, and remediation workflows, allowing security teams to focus on what truly matters.
Top Vulnerability Management Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Tenable Nessus | Comprehensive vulnerability scanning, plugin-based engine | SMBs to enterprises | Detecting outdated software versions across 1,000+ corporate endpoints |
| Rapid7 InsightVM | Live asset discovery, risk-based prioritization | Dynamic networks | Remediating high-risk CVEs across hybrid cloud environments |
| Qualys VMDR | Integrated scanning, patching, and asset inventory | Compliance-focused teams | Automating patch deployment for PCI-DSS compliance |
| OpenVAS (Greenbone) | Open-source, customizable scanning engine | Security researchers, budget-conscious orgs | Scanning internal networks for misconfigurations and weak services |
| BeyondTrust Retina CS | Centralized vulnerability & configuration management | Enterprises with legacy systems | Identifying exploitable legacy applications in industrial control systems |
With attack surfaces expanding daily, vulnerability management tools are vital for staying ahead of threats and ensuring your systems are not the low-hanging fruit attackers exploit.
Data Loss Prevention (DLP) Tools

In an era where data is more valuable than gold, protecting it from accidental leaks or malicious exfiltration is paramount. Whether it’s sensitive customer information, proprietary code, or regulated financial records, organizations must ensure data stays where it belongs. Data Loss Prevention (DLP) tools are built for this purpose.
DLP tools monitor, detect, and block unauthorized data movement—across endpoints, networks, cloud apps, and storage. In 2025, advanced DLP solutions integrate with CASBs, encryption, and identity controls to enforce policies in real time and maintain regulatory compliance (e.g., GDPR, HIPAA, PCI-DSS).
Top DLP Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Symantec DLP (Broadcom) | Policy-based control, fingerprinting, cloud & endpoint visibility | Enterprises & compliance-heavy orgs | Blocking credit card numbers from being emailed externally |
| Forcepoint DLP | Behavior analytics, risk-adaptive protection | Organizations with insider threat risk | Stopping disgruntled employee from transferring IP to USB |
| Digital Guardian | Agent-based control, encryption, real-time monitoring | Manufacturing, legal, finance | Securing CAD files and trade secrets from unauthorized sharing |
| Microsoft Purview DLP | Native integration with M365, auto-labeling, policy tips | Microsoft 365 environments | Preventing confidential reports from being uploaded to personal cloud |
| McAfee Total Protection DLP | Unified control across endpoints, cloud, and network | Global enterprises | Blocking confidential data in outbound FTP or email traffic |
DLP tools are your last line of defense—ensuring that sensitive data doesn’t leave your organization, whether through negligence, error, or malicious intent.
Firewall & Network Security Tools

Every piece of data entering or leaving a network is a potential threat vector. That’s why network security tools and firewalls remain foundational to modern cybersecurity architectures. These tools monitor, filter, and block malicious traffic—before it ever reaches your applications, systems, or users.
In 2025, firewalls have evolved far beyond simple port-blocking. Today’s solutions incorporate deep packet inspection, intrusion prevention, application-level filtering, and AI-based threat analysis. Combined with SD-WAN, VPN, and Zero Trust integrations, modern firewalls help secure complex, distributed infrastructures.
Top Firewall & Network Security Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Palo Alto Networks NGFW | App-ID technology, threat prevention, Zero Trust architecture | Large enterprises | Segmenting user access based on app identity across multiple data centers |
| Fortinet FortiGate | High-throughput firewall, SD-WAN, deep inspection | Multi-branch organizations | Securing network edges in a global retail operation |
| Cisco Secure Firewall | Layer 7 inspection, encrypted traffic analytics, VPN support | Cisco-based infrastructures | Monitoring east-west traffic between microservices |
| Check Point Quantum | Unified threat prevention, cloud security, performance tuning | High-performance workloads | Blocking known malware and command-and-control communication attempts |
| pfSense (Netgate) | Open-source, highly configurable, strong community support | SMEs and tech-savvy admins | Managing affordable network segmentation and remote access policies |
Whether cloud-native or hardware-based, firewalls remain the gatekeepers of your digital perimeter—protecting infrastructure, enforcing policy, and stopping unauthorized access.
SOAR Tools

When security alerts pour in from multiple systems—endpoints, firewalls, SIEMs, cloud platforms—analysts can quickly become overwhelmed. That’s where SOAR (Security Orchestration, Automation, and Response) tools step in to help organizations scale their incident response and reduce time to resolution.
SOAR platforms allow security teams to automate repetitive tasks, create response playbooks, and orchestrate actions across multiple tools. In 2025, with the average time to detect a breach still measured in days or weeks, SOAR has become essential for streamlining workflows and cutting down response lag.
Top SOAR Tools in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| Palo Alto Networks Cortex XSOAR | Drag-and-drop playbook builder, threat intel integration | Large-scale, mature SOCs | Automating response to phishing emails using enrichment, blocklists, and ticketing |
| IBM SOAR (Resilient) | Case management, orchestration, dynamic playbooks | Regulated industries | Coordinating breach response workflows across HR, legal, and IT |
| Splunk SOAR (formerly Phantom) | Real-time automation, visual workflow editor | Organizations already using Splunk | Integrating with Splunk SIEM to auto-quarantine compromised endpoints |
| Tines | No-code automation, API-first architecture | Agile security teams | Creating lightweight automations for alert triage from Slack and Jira |
| DFLabs IncMan SOAR | Threat triage, KPI tracking, customizable runbooks | MSSPs and large enterprise SOCs | Reducing manual triage time by triggering predefined enrichment and containment steps |
SOAR tools are no longer optional for modern cybersecurity teams—they enable faster, more consistent, and more intelligent incident response, helping organizations do more with less.
Threat Intelligence Platforms (TIPs)

In cybersecurity, context is power. Knowing who is attacking, what tactics they’re using, and where they’ve been spotted can help security teams stay one step ahead. That’s exactly what Threat Intelligence Platforms (TIPs) deliver.
TIPs centralize and enrich threat data from multiple sources—such as open-source feeds, commercial vendors, and internal logs—and transform it into actionable intelligence. These platforms streamline threat detection, improve SIEM and SOAR performance, and support proactive defense strategies.
In 2025, with threats evolving faster than ever, TIPs are essential for building a threat-informed security posture.
Top Threat Intelligence Platforms in 2025
| Tool Name | Key Features | Best For | Real Use Case |
|---|---|---|---|
| ThreatConnect | Threat intelligence lifecycle management, integrations with SIEM/SOAR | Enterprise threat teams | Enriching SOC alerts with context from nation-state and ransomware IOCs |
| Anomali ThreatStream | Aggregated intel feeds, machine learning correlation | MSSPs and large enterprises | Correlating global threat data to detect targeted phishing campaigns |
| Recorded Future | Real-time threat intel, dark web monitoring, risk scoring | Financial and government sectors | Tracking leaked credentials and attacker chatter relevant to your organization |
| MISP (Open Source) | Threat sharing, automation support, community-driven | NGOs, academia, budget-conscious orgs | Sharing intel between multiple CERTs or regional cybersecurity teams |
| IBM X-Force Exchange | Global intel database, collaborative tools, malware sandboxing | Organizations using IBM ecosystems | Integrating threat reports into QRadar for faster detection of known IOCs |
TIPs help security teams move from reactive defense to predictive insight, enabling smarter decision-making and faster, targeted responses.
Conclusion: Why Choosing the Right Cybersecurity Tools Matters
In 2025, cybersecurity is no longer just about blocking threats—it’s about building a layered, intelligent defense ecosystem. From SIEM and SOAR to endpoint protection, threat intelligence, and DLP, each cybersecurity tool plays a specific role in strengthening your security posture.
But not every organization needs the same stack. Choosing the right mix depends on your infrastructure, compliance needs, internal capabilities, and threat landscape. What’s consistent across the board is this: cybersecurity tools are no longer optional—they’re fundamental to business survival.
By understanding how each tool functions and complements the others, organizations can proactively defend against cyber threats, reduce incident response time, and protect their most valuable assets—data, people, and reputation.
FAQ About Best Cybersecurity Tools
What are the most essential cybersecurity tools in 2025?
The most essential cybersecurity tools in 2025 include SIEM systems, endpoint protection platforms, SOAR tools, DLP solutions, and threat intelligence platforms. Together, they provide visibility, automation, and protection across the entire attack surface.
How do cybersecurity tools work together?
Cybersecurity tools work best when integrated—SIEM collects logs, SOAR automates response, EDR blocks threats, and TIPs provide context. This synergy reduces alert fatigue, speeds up incident response, and improves overall threat visibility.
Are open-source cybersecurity tools effective in 2025?
Yes, many open-source cybersecurity tools like Snort, Suricata, and MISP offer enterprise-grade capabilities. However, they often require skilled teams for proper implementation, integration, and maintenance.
How do I choose the right cybersecurity tool for my organization?
Start by identifying your risk areas, compliance requirements, and existing tech stack. Then evaluate cybersecurity tools based on scalability, integration capabilities, vendor support, and use cases relevant to your industry.
Do small businesses need cybersecurity tools?
Absolutely. Cyber threats don’t discriminate by size. In fact, small businesses are often targeted due to weaker defenses. Even basic cybersecurity tools—like firewalls, antivirus, and secure email gateways—can significantly reduce risk.




